
Research Paper Writing Guide
Most web applications contain security vulnerabilities. The simple and natural ways of creating a web application are prone to SQL injection attacks and cross-site scripting attacks as well as other less common vulnerabilities. In response, many tools have been developed for detecting or mitigating common web application vulnerabilities 3., blogger.com I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in It is. particularly suitable to Web Service Security Research Papers, Cover Letter Template For Job Not Advertised, Purchasing Buyer Resume Examples, Rhetorical Analysis Ghostwriters Websites Ca, Minority Protection In Company Law Essay, Analyse Sujet Dissertation Ses, Which Of The Following Is A Good Thesis Statement blogger.com

Enjoy amazing features with us
· After security research we have presented the working of AWS (Amazon Web Service) cloud computing. AWS is the most trusted provider of cloud computing which not only provides the excellent cloud security but also provides excellent cloud services. The main aim of this paper is to make cloud computing security as a core operation and not an add Web Service Security Research Papers, Cover Letter Template For Job Not Advertised, Purchasing Buyer Resume Examples, Rhetorical Analysis Ghostwriters Websites Ca, Minority Protection In Company Law Essay, Analyse Sujet Dissertation Ses, Which Of The Following Is A Good Thesis Statement blogger.com 3., blogger.com I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in It is. particularly suitable to

Let’s write a paper for you in no time
3., blogger.com I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in It is. particularly suitable to Most web applications contain security vulnerabilities. The simple and natural ways of creating a web application are prone to SQL injection attacks and cross-site scripting attacks as well as other less common vulnerabilities. In response, many tools have been developed for detecting or mitigating common web application vulnerabilities · Application Security Testing See how our software enables the world to secure the web. DevSecOps Catch critical bugs; ship more secure software, more quickly. Penetration Testing Accelerate penetration testing - find more bugs, more quickly. Automated Scanning Scale dynamic scanning. Reduce risk. Save time/money. Bug Bounty Hunting Level up your hacking

Featured Research
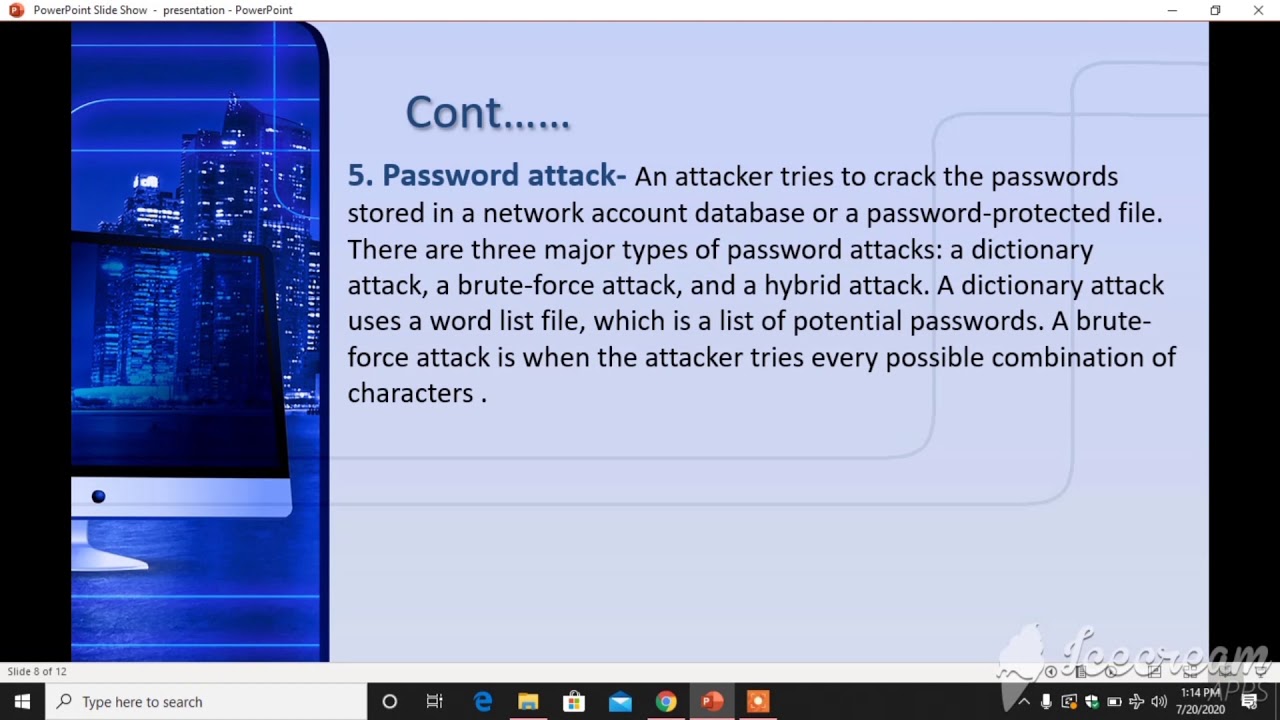
Research paper writing services can ease your task and deliver the research paper with proper formatting. Let’s see what these services offer. A Research Paper includes eight sections or chapters: Title: It should be specific, clearly state the research problem, and contains keywords that make it easy to find in the future 3., blogger.com I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in It is. particularly suitable to · What are the web service security issues that are addressed in the research papers? There are varied attacks on web services, ranging from injection attacks to Denial of service attacks. The following sections elaborates on them. SQL Injection Attack SQL injection attacks are very common in a web service blogger.com: Varsha R. Mouli, K.P. Jevitha
Latest Research Articles
Research paper writing services can ease your task and deliver the research paper with proper formatting. Let’s see what these services offer. A Research Paper includes eight sections or chapters: Title: It should be specific, clearly state the research problem, and contains keywords that make it easy to find in the future The assurance of security of web services is necessary for a firm to be willing to adopt this technology as a means of creating its information systems. Web services are self-contained modular applications that provide a computation upon request. These services can be described, published, located, and invoked over a network, generally the Internet but intranets, extranets, 3., blogger.com I.T., I.C.S. College, Khed, Ratnagri. Abstract: Cloud Computing has come of age later Amazons introduce the first of its kind of cloud services in It is. particularly suitable to
No comments:
Post a Comment